How to track down "Silk Road" hackers? Ouke Cloud Chain Research Institute: On chain data is a key capability
In July, the US government (USG) converted nearly 8200 BTCs into exchanges, which attracted market attention, and the large amount attracted public attention. The US government is the world's largest Bitcoin holder, with approximately 200000 Bitcoins seized from cybercrime or hidden networks and controlled by the Department of Justice, the Internal Revenue Service, or other agencies

In July, the US government (USG) converted nearly 8200 BTCs into exchanges, which attracted market attention, and the large amount attracted public attention. The US government is the world's largest Bitcoin holder, with approximately 200000 Bitcoins seized from cybercrime or hidden networks and controlled by the Department of Justice, the Internal Revenue Service, or other agencies. According to data provided by OKLink, this year is not the first time the US government has sold BTC.
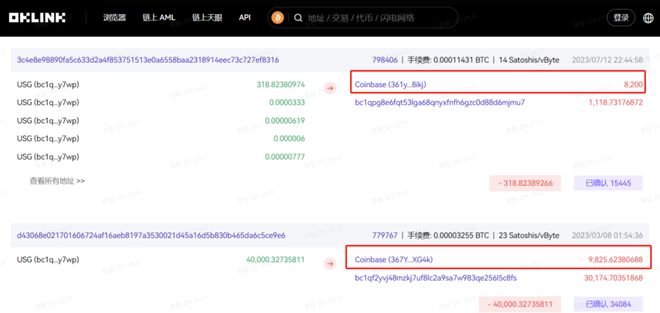
Resource: OKLinkExplorer
Recently, CNBC reported that Chinese American youth Jimmy Zhong (abbreviated as Zhong) had stolen nearly 53000BTC from SilkRoad, revealing the second largest source of Bitcoin by the US government and the bizarre incident of hackers stealing dark networks. Let's take a look at how Zhong stole a huge amount of Bitcoin and how he was eventually caught.
Hackers exploit vulnerabilities to obtain huge profits
In 2012, Zhong discovered a vulnerability in the Silk Road (Dark Web), which confused the website system by triggering 140 transactions in a row, extracting over 53000 BTCs. For example, on September 19, 2012, Zhong deposited 500 Bitcoins from the address mentor into the SilkRoad wallet. Less than five seconds after the first deposit, Zhong quickly and continuously performed five withdrawals of 500 Bitcoin in the same second, resulting in a net profit of 2000 Bitcoin, as shown in the following figure:

After stealing a huge amount of Bitcoin, Zhong remained very cautious and did not immediately use the funds, maintaining his previous address and clothing. Between December 2020 and January 2021, Zhong transferred 750BTC to a currency mixer, confusing and disrupting the flow of funds, making it more difficult to track funds, as shown in the following figure:
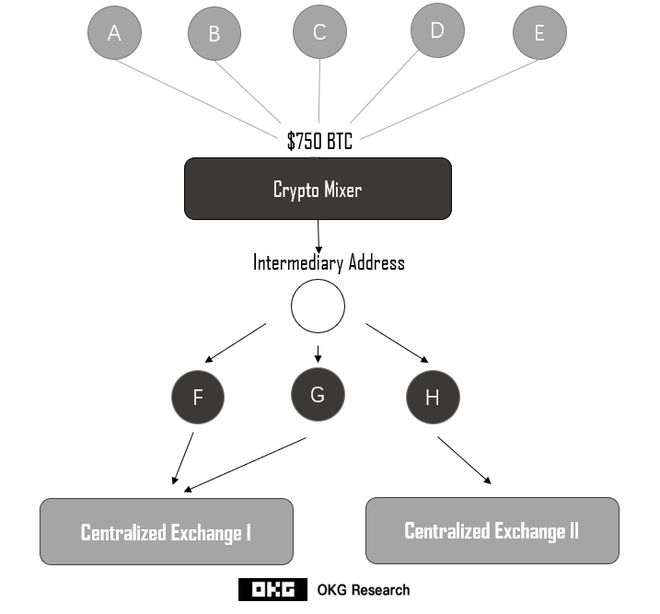
On chain data helps judicial authorities recover funds
Matthew Price, former head of investigation at the IRS, once said that when Bitcoin is stolen nowadays, the culprit is like a person robbing a bank in the snow. No one may know the name of the culprit, but the traces left by the digital field, like footprints on the snow, can still be traced by the authorities.
So even if Zhong did it meticulously, there were still some omissions. Initially, he deposited 50000 Bitcoin into two separate wallets, with 10000 BTC wallets being transferred to 10 wallet addresses in batches, each with 1000BTC. But there is a wallet address with 0.0775 BTCs that interacts with the centralized exchange.
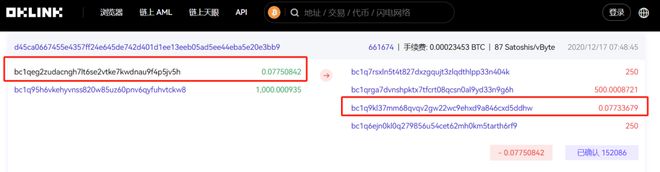
Source: OKLinkExplorer
Nowadays, the anonymity of Bitcoin has greatly decreased, and the crime of using Bitcoin for transactions in dark networks has also greatly decreased, as each transaction is permanently stored in the blockchain's ledger. For example, in OKLink's Chaintellengence, the primary address bc1q for Zhong The black address label labeled on 30ch allows relevant institutions or government agencies to use their monitoring system to automatically monitor the address (as shown in the figure below). Once the address interacts with other addresses or entities, the institution or government agency will receive an alert.
*Zhong concentrated the stolen BTCs into two wallets, each containing 40000 and 10000 BTCs. The address is the wallet where 40000 BTCs are stored.
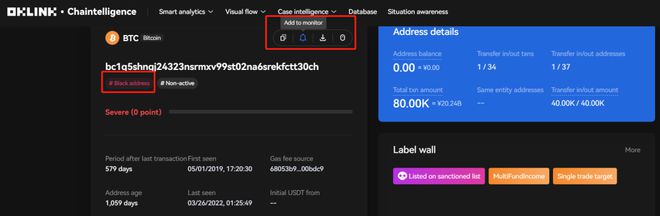
Source: Chaintelligence Pro
Although the incident has been going on for a long time, relying on the online service provider, the police became aware of this transfer and through the wallet X that interacted with the exchange, the investigators found Zhong. Through this part of the "footprint" on the chain, they traced the wallet E and other money packages, as shown in the following figure:

Zhong also lost assets worth $3.3 billion due to a BTC worth $800 (0.0775 BTC).
Is the funds flowing into the coin mixer at large?
Briefly introduce the business process of a coin mixer. Taking TornadoCash as an example, if a user wants to transfer an asset anonymously or mix coins, they first need to transfer the asset to TornadoCash's smart contract, mix the funds, and then return them to the user. During the process, the coin mixer will give the user a key as a credential to prove your deposit; When retrieving, only the random key given by the system before submission is required, and after submitting a new address, the smart contract will transfer the asset to the new address and complete the "mixed currency" of the asset.
According to the above introduction, money that has been cleaned by the coin mixer also needs to interact with the new address before it can be transferred. So on chain data companies can use the interaction behavior between the address and the mixer to mark it with a black address or label it after interacting with the mixer. When these addresses interact with the exchange, the exchange or agency unit using the on chain service can be notified, even if the entire process cannot be replicated, it can penetrate some sources of funds.

In this game with black and gray funds, the capacity of data on the chain is the most crucial. Having more data means that we have a clearer picture of the flow of funds and the underlying entities. OKLink has invested a lot of time and effort in this area, and can now cover over 170 blockchain networks with over 3.5 billion address tags, including nearly 70 million black and gray address tags.
Based on the underlying data mentioned above, OKLink can increase the interactivity, application scope, and application depth of on chain tracing through Chaintelligence, distinguishing legitimate and suspicious assets. At the same time, it can also depict the real identity through exchanges that convert cryptocurrency into cash. At the same time, we will collaborate with Onchain AML to combat money laundering activities, safeguard financial security on the chain, and meet regulatory compliance requirements.
reference
2. U.S. Attention AnnouncesHistorical $3.36 BillionCryptocurrencySeizureAndConfectionInConnectionWithSilkRoadDarkWebFraud:
https://www.justice.gov/usao-sdny/pr/us-attorney-announces-historic-336-billion-cryptocurrency-seizure-and-conviction
3. AffidavitinSupport of Government's ForfeatureMotion:
https://www.justice.gov/d9/press-releases/attachments/2022/11/07/ecf_394-5_agent_affidavit.pdf
Tag: How to track down Silk Road hackers Ouke Cloud
Disclaimer: The content of this article is sourced from the internet. The copyright of the text, images, and other materials belongs to the original author. The platform reprints the materials for the purpose of conveying more information. The content of the article is for reference and learning only, and should not be used for commercial purposes. If it infringes on your legitimate rights and interests, please contact us promptly and we will handle it as soon as possible! We respect copyright and are committed to protecting it. Thank you for sharing.


